

Decrypt Sql Password
Hashing algorithms
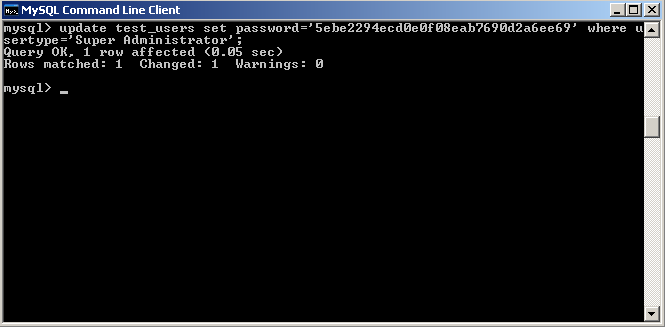
How To Decrypt Encrypted Password
Call of duty mw2 trainer pc games. The Apache HTTP Server can use a.htpasswd file referenced from a.htaccess file to create restricted protected areas. The.htpasswd file contains rows corresponding to a pair of username and password separated with a colon character. The password is encrypted using the UNIX system's crypt method and may use MD5 or SHA1. Autoturn 9.0 cd key. This.htpasswd generator creates passwords that are hashed. Htpasswd returns a zero status ('true') if the username and password have been successfully added or updated in the passwdfile.htpasswd returns 1 if it encounters some problem accessing files, 2 if there was a syntax problem with the command line, 3 if the password was entered interactively and the verification entry didn't match, 4 if its operation was interrupted, 5 if a value.
How To Decrypt Htpasswd Passwords
- bcrypt $2y$ or $2a$ prefix
- This algorithm is currently considered to be very secure. Bcrypt hashes are very slow to compute (which is one one the reasons why they are secure). The cost parameter sets the computing time used (higher is more secure but slower, default: 5, valid: 4 to 31).
Warning : think carefully before you try values above 10, this thing is really slow. You could freeze your computer.
Compatibility : Apache since version 2.4 (needs apr-util 1.5+) - md5 (APR) $apr1$ prefix
- Apache-specific algorithm using an iterated (1,000 times) MD5 digest of various combinations of a random salt and the password. This is the default (since Apache version 2.2.18).
Compatibility : all Apache versions, Nginx 1.0.3+. - crypt(), also known as crypt(3) no prefix
- It used to be the default algorithm until Apache version 2.2.17. It limits the password length to 8 characters. Considered insecure.
Compatibility : all Apache and Nginx versions, Unix only. Plain ASCII characters only. - salted sha-1 {SSHA} prefix
- Considered insecure. The use of salt makes it more time-consuming to crack a list of passwords. However, it does not make dictionary attacks harder when cracking a single password.
Compatibility : Nginx 1.0.3+ only. - sha-1 {SHA} prefix
- Facilitates migration from/to Netscape servers using the LDAP Directory Interchange Format (ldif). This algorithm is insecure by today's standards.
Compatibility : all Apache versions, Nginx 1.3.13+. - Plaintext (no hashing) no prefix for Apache, {PLAIN} for Nginx
- Use plaintext passwords. Insecure.
Compatibility : all Windows and Netware Apache versions, Nginx 1.0.3+.